
What is Crimeware?
October 06, 2023
Crimeware is a specific noun that means all malicious software that is applied in cyberattacks. The vast majority of the viruses spread in the modern computer environment can be called crimeware, but that term has not caught on. People used the older umbrella terms, like malware or computer virus, even though they are not 100% true as well. Let’s check out this historical phenomenon.
Malware as a tool for earning money appeared in the mid-’00s. Initially, crooks were receiving money as a bank transfer or a mobile number top-up - since banks’ transaction monitoring was way weaker. Around that time, the virus as malware type became so widespread that its name became a common noun for any malicious program. In fact, viruses almost ceased to exist around 2010, after several fundamental improvements in detection mechanisms.
Centralised cybercrime appeared around the end of the ‘00s and led to the appearance of malicious tools that were created specifically for the hackers’ needs. Contemporary malware, made without a certain order was still acceptable, but it was obvious that there could be much better efficiency. Besides the malware types that were adopted to that category, several categories of malware appeared specifically after the requirements of hackers.
Currently, analysts define the following malware types that fall under the definition of crimeware:
- Ransomware;
- Malware Downloader;
- Spyware;
- Backdoor;
- Coin Miner;
- Adware.
What are crimeware attacks?
As you can guess from the paragraphs above, crimeware attacks are cyber offenses that are committed with the help of crimeware. The latter is not used solitarily - crooks usually apply different tools, depending on the attack target and the target's toughness. Besides the malware types mentioned above, there is also a lot of dual-purpose software. In particular, crooks use tools for hacking the Windows passwords, monitoring the opened network ports, establishing the connection with the command center, and escalating the privileges. Most of these apps are classified as unwanted programs - even when they may be applied for civil use.
The typical cyberattack with the use of crimeware is a well-planned operation. These days, many crimeware examples are made to satisfy the hackers’ needs for just a single attack. Malicious software is created to be effective only in the environment of an attacked corporation. And to be sure about the effectiveness of such an approach, rascals should know a lot about the target organization . Preparing the attack requires diligent reconnaissance - it is usually done with OSINT.
Delivery vectors
The most important part of any cyberattack is delivering the payload if it is supposed. DDoS attacks are still intact and it is important to keep them in mind. They usually aim only on mischief and spoiling the image of the target. Crimeware is designed to be as automated as possible, so hackers may just lean back on the chair and relax after a successful attack. However, before spectating the result of the injection, , they should drop a lot of sweat to bypass the security mechanisms. Not all companies have such protection systems that can be a serious obstacle for hackers, but the activities must remain stealthy. Any excessive noise is a potential trigger for qualified personnel to start manual actions.
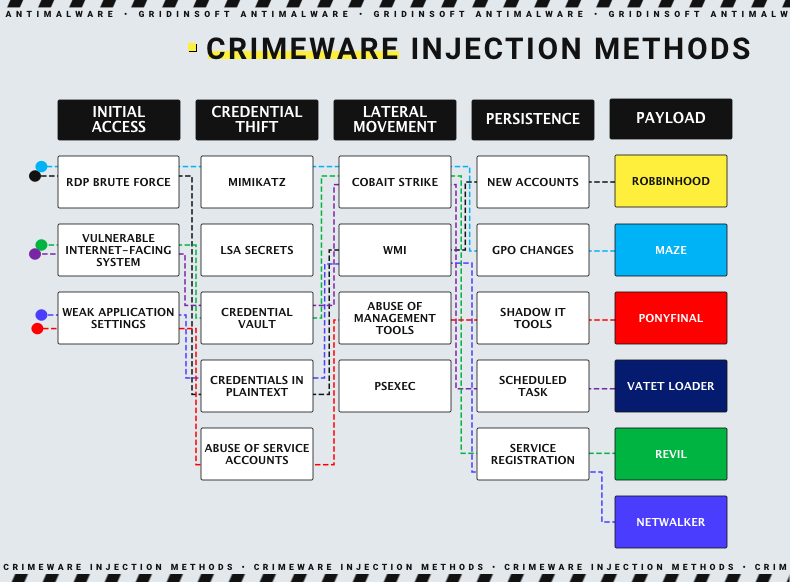
The typical vectors for crimeware delivery are vulnerable RDP ports and spam emails. The first one supposes connecting to the remote desktop through an unsecured port and brute-forcing the login credentials. Email spamming, on the other hand, involves sophisticated phishing tactics that must trick an employee to open the attached file. In that file, the downloading script for crimeware is hidden.
Crimeware attacks variations
In rare cases, for example, when the crooks plan to stay in the network for a long time, the final payload injection may happen months after getting access to the network. That access is gained with the methods as mentioned above - primarily by exploiting the RDP breaches or ones in other software products. Typically, crooks use this time gap to find and steal all valuable data they can reach and spy on the internal processes inside the company.
DDoS attacks are a particular case of crimeware applications when the offense's target is to make the server inoperable without getting into the network. Creating a huge wave of requests overflowing the servers may look like an amateur tactic that does not require much effort and technical advancements. However, they should be skilled enough to bypass the modern systems that mirror the botnets without giving them a chance to connect to the target server. Additionally, there are dozens of different ways to commit the DDoS-attack - so hackers have to choose their option as well.
Consequences of crimeware attacks
The consequences of crimeware attacks may vary depending on the initial target the crooks were intended to reach. Crimeware as an instrument of cybercrime will likely do only what it was created for, without any additional damage. Hence, we can suppose the following effects of the cyberattack:
- Data breach. It usually happens after the spyware activity in the network. Using it, crooks download all information they count as valuable on their servers or to the cloud storage.
- Data ciphering. Ransomware is the other often guest of cyberattacks. A lot of cybercriminals practice so-called double extortion, which means paying not only to keep the leaked data unpublished but also to decrypt the data on the company’s local storage.
- Reputational losses. Loud names always try to keep their image well, with regular proof about the safety of their client's data. Still, that does not mean crooks will never find a way to get in. Publishing the case of a successful data leak in the company that claims its hack-proofness will cost the latter a lot of money - to wash out the image of a reliable company. This sort of losses gave birth to the triple extortion. Hackers blackmail the companies they managed to break in to receive the additional sum for keeping the cybersecurity incident secret.
- Traffic losses. In the case of a DDoS attack, the attacked website or server may be inaccessible to everyone, or to the users from a certain range of IP addresses. That decreases the traffic, and the overall downtime of the server makes the site's position in search engines much lower.
It's worth noting that you should sum up those consequences in most cases. One-vector cyber attacks happen pretty rarely, so in most cases, hackers will apply ransomware, spyware, and exploit malware, creating a synergy of effects. Sometimes, crimeware may contain all things simultaneously in a single program - but it is much easier to counter.
How to prevent crimeware attacks?
Preventing the attacks with the use of crimeware differs from cybersecurity for single users. Since crooks usually target their attacks and do a survey of the company they aim for, the corresponding actions should be taken. Still, some advice may be the same for all users - the same basic cybersecurity rules apply to everyone.
- Instruct your employees about cybersecurity threats. The biggest security breach that is impossible to fix with a software patch is an employee who clicks whatever it sees. Raising personnel awareness will reduce crooks by around 40% of possible injection methods. Explain how to distinguish a fake email and forbid launching the attached files unless you are sure about the sender.
- Decrease the privileges. Most of the crimeware requires administrator privileges to launch. Even though crooks may still manage to get the admin privileges through exploits, that will confuse them and force them to improvise, giving you more time to counteract. Overall, managing the access rights and privileges in terms of cybersecurity is a very effective practice.
- Update your software as often as possible. The thing that is used in a huge number of cyberattacks is software exploitation. Software vendors have bug-hunter teams that look for possible breaches to find and fix them before the crooks do. Usually, vendors notify about urgent updates on their official pages on social media.
- Use advanced protection systems. Endpoint Detection and Response (EDR) systems will effectively manage your organization's cybersecurity aspects. The zero-trust ideology that is often applied in those solutions will nail the crooks' chances to act spontaneously. Contrary to the use of separated security tools on each machine in the network, using the EDR will create a dome that will control all devices simultaneously.